Trezor Login: Secure Your Crypto Effortlessly
A complete guide for beginners to access and manage your Trezor wallet safely
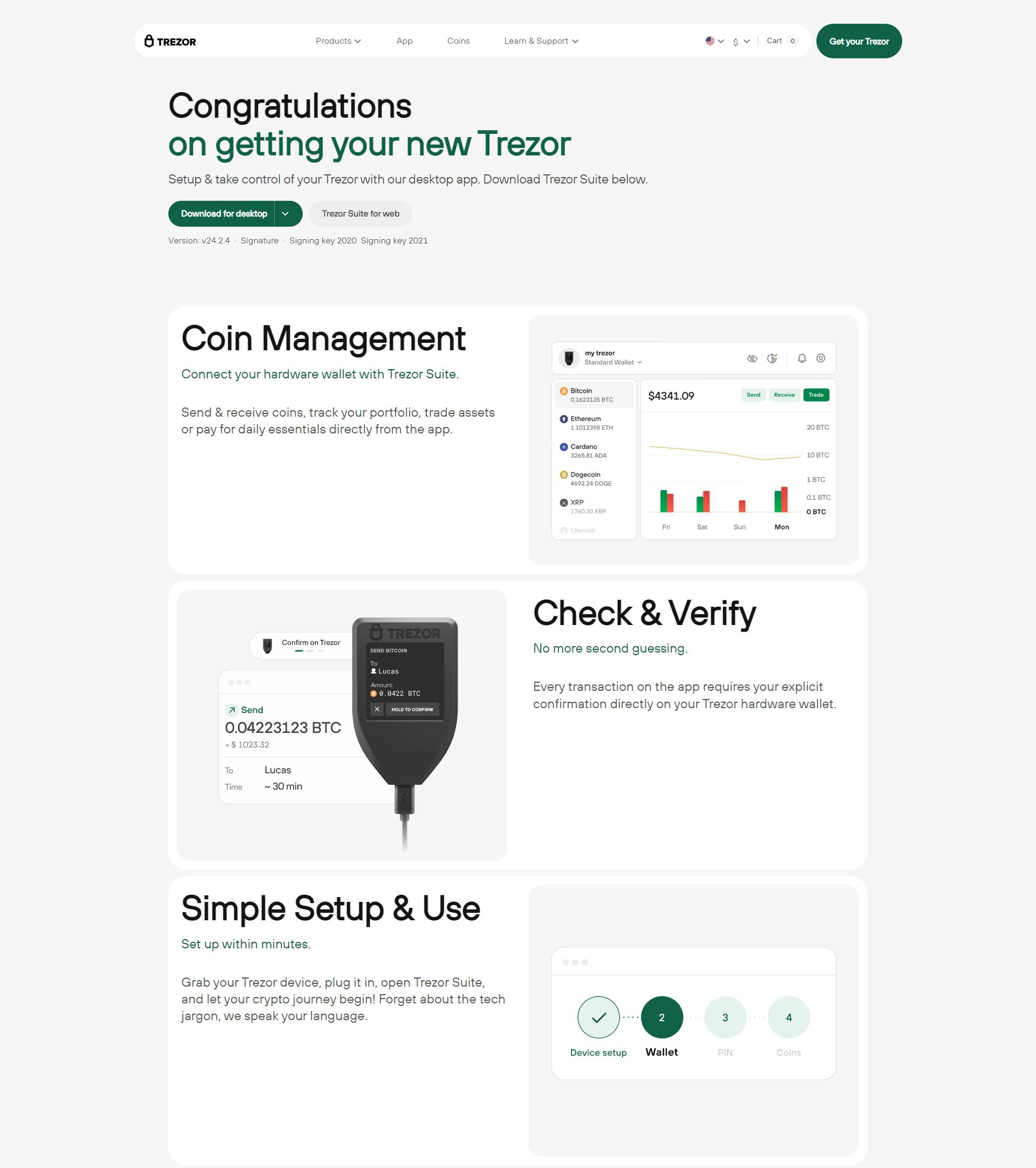
Understanding Trezor Wallets
Trezor wallets are hardware devices designed to store cryptocurrency private keys securely offline. Think of them as a digital vault, isolated from the internet, preventing hackers from accessing your funds. With over 10+ supported cryptocurrencies and an easy-to-use interface, Trezor has become a go-to option for both beginners and seasoned crypto enthusiasts.
Key features include:
- Offline private key storage
- Multi-coin support
- Recovery seed protection
- User-friendly interface
- Advanced security measures
Why Secure Login Matters
Your Trezor login is the gateway to your digital assets. Using secure login practices is crucial to avoid phishing attacks, malware, and other cyber threats. Always ensure:
- Your device firmware is updated
- Your recovery seed is never shared or stored digitally
- Use strong and unique passwords for Trezor Bridge or wallet apps
By following these precautions, you are effectively reducing the risk of crypto theft and maintaining the integrity of your assets.
Step-by-Step Trezor Login Guide
Common Issues and Troubleshooting
Even with simple steps, users may encounter login issues. Here’s how to tackle them:
- Device Not Recognized: Ensure Trezor Bridge is installed and updated.
- Incorrect PIN: Trezor allows retries but reset your device if locked.
- Browser Compatibility: Use Chrome, Firefox, or Edge for best results.
- Firmware Update: Sometimes updating the device resolves connectivity issues.
Trezor vs Other Hardware Wallets
| Feature | Trezor | Ledger |
|---|---|---|
| Supported Coins | 1000+ | 1500+ |
| Open Source Firmware | Yes | No |
| Ease of Use | Beginner-friendly | Intermediate |
| Price | $70–$200 | $60–$180 |
Pro Tips for Beginners
- Always back up your recovery seed securely offline.
- Use a separate password manager for your wallet credentials.
- Test small transactions before transferring large sums.
- Stay updated with Trezor firmware and app updates.
- Consider using a hardware wallet in combination with cold storage for maximum security.
FAQs About Trezor Login
No, Trezor Bridge is required to facilitate secure communication between your device and browser.
You can reset the device, but ensure you have your recovery seed to restore your funds.
Yes, Trezor Suite supports mobile devices via USB-C or OTG adapters.
Extremely secure, as your private keys never leave the device and login PIN is entered physically on Trezor.
Conclusion
Trezor login is more than just entering a PIN; it’s your first line of defense in safeguarding digital assets. By understanding its functionality, following step-by-step procedures, and adopting best practices, you can confidently manage your cryptocurrency portfolio. Whether you’re a beginner or an intermediate crypto user, Trezor ensures a secure, user-friendly experience, keeping your investments protected while offering easy access whenever needed.
Start your secure crypto journey today with Trezor login!